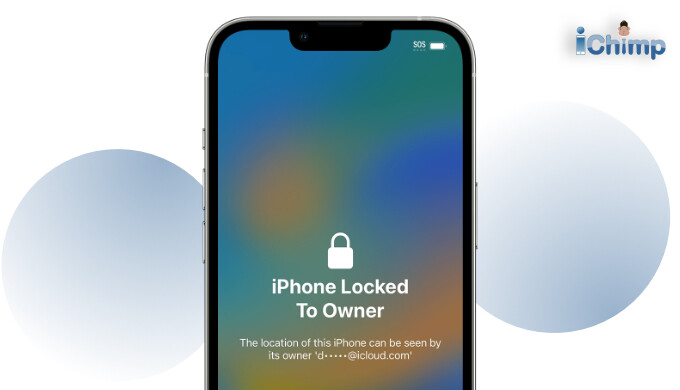
Bypass
**Bypass: Unlocking Hidden Security Measures and Overcoming Restrictions**
Learn how to bypass security measures, gain access to restricted content, and overcome limitations in various contexts. Explore methods for bypassing firewalls, network filters, authentication mechanisms, and even physical barriers. Discover the tools and techniques employed by security professionals and ethical hackers to navigate complex systems and information locks. This post delves into the ethical considerations, potential risks, and legal implications of bypassing security measures. Whether you’re a cybersecurity enthusiast, penetration tester, or simply seeking to expand your knowledge, “Bypass” provides valuable insights into the art of bypassing restrictions and unlocking hidden paths.